[ad_1]
Google-owned safety agency Mandiant spent a number of hours attempting to regain management of its account on X (previously often known as Twitter) on Wednesday after an unknown scammer hijacked it and used it to unfold a hyperlink that tried to steal cryptocurrency from individuals who clicked on it.
“We’re conscious of the incident impacting the Mandiant X account and are working to resolve the problem,” firm officers wrote in a press release. “We have since regained management over the account and are at the moment engaged on restoring it.” The assertion didn’t reply questions asking if the corporate had decided how the account was compromised.
The hacked Mandiant account was initially used to masquerade as one belonging to Phantom, an organization that provides a pockets for storing cryptocurrency. Posts on X inspired individuals to go to a malicious web site to see if their pockets was one among 250,000 that have been eligible for an award of tokens. Over a number of hours, X staff performed tug-of-war with the unknown scammer, with rip-off posts being eliminated solely to reappear, based on individuals who adopted the occasions.
-
Mandiant profile web page claiming to be affiliated with “pleasant crypto pockets” Phantom.
-
One of many rip-off posts unfold by the hijacked Mandiant account.
Finally, the scammer modified the @mandiant username and reappeared below a brand new username. After utilizing the account to advertise a faux web site impersonating Phantom and promising free tokens, it posted the cryptic message: “verify bookmarks once you get account again.” It additionally chided Mandiant to “change password please.”
-
Put up saying “change password please”
-
Put up saying to verify bookmarks
On the time this publish went dwell on Ars, the Mandiant profile displayed the message “This account doesn’t exist.”
Mandiant is without doubt one of the main safety firms and greatest recognized for serving to purchasers examine and get well from main community compromises. That vantage level provides it main insights into menace actors, lots of them backed by nation-states, and the customarily beforehand unknown ways, strategies, and procedures they use to compromise the safety of among the world’s strongest and well-resourced organizations. Google bought Mandiant in 2022 for $5.4 billion, which, on the time, was its second-biggest acquisition ever.
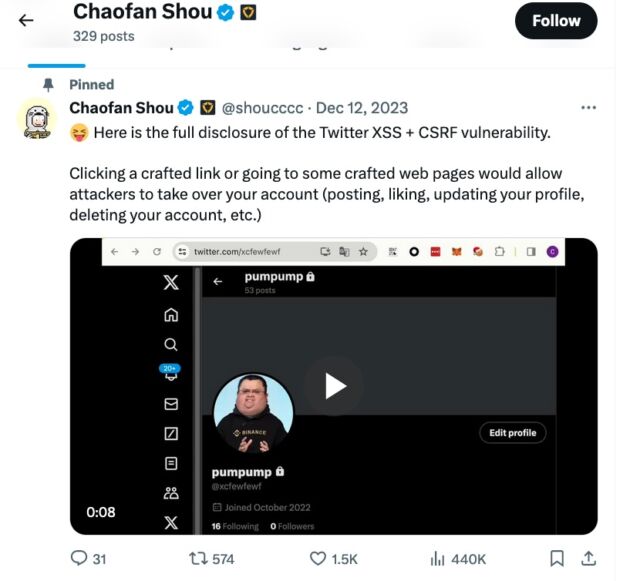
Many questions stay about Mandiant’s measures to safe its X account. Amongst them: Was it protected by a powerful password and any type of two-factor authentication? Final month, somebody claimed to have found the social media website was susceptible to a “mirrored XSS,” a kind of vulnerability that may typically be used to compromise the safety of accounts when a professional person at the moment logged in clicks on a malicious hyperlink in a special browser tab. The person stated they reported the vulnerability by professional channels however that the submission didn’t qualify below the X bug bounty program.
“Clicking a crafted hyperlink or going to some crafted internet pages would enable attackers to take over your account (posting, liking, updating your profile, deleting your account, and so forth.),” Chaofan Shou, a College of California at Berkeley Ph.D. candidate, wrote final month.
Makes an attempt to achieve Phantom for remark have been unsuccessful.
[ad_2]